About 30,000 websites get hacked every day. That’s what Forbes data stated.
A hacker attack is such a nightmare of ecommerce, which consequently drives unpredictable losses for both businesses and their customers. Tokopedia – Indonesia’s largest ecommerce platform, has recently investigated a hack on their website, in which the personal details of 15 million users were leaked (including names, emails, and birthdays). Fortunately, user passwords and payment information remained secure. It would be such a bitter pill for the firm to drink if even all credentials were leaked.
Not only big firms are the victims of e-commerce security threats; small merchants are more vulnerable ones with cybercrimes. This rushes us to summarize the most common risks that every ecommerce website may encounter.
I – Most Common Ecommerce Security Threats
Table of Contents
1.1 Credit card hijacking

Ever since the first ecommerce website was launched, financial frauds have been giving online merchants a headache because hackers create unauthorized transactions and wipe out the trail causing significant losses for businesses.
Credit card data (credit card hijacking) is always the most lucrative target of cybercriminals. This fraud happens due to a known vulnerability that allows attackers to inject malicious JavaScript code into online checkout software systems and hack payment data coming through your shopping cart. Once credit card data is hacked, attackers may exploit them to make purchases on your website.
The biggest dangers of credit card hijacking is that it can go undetected for a long time, expose confidential data like payment information, and put your customers’ data at risk.
One of the predictable signs of a credit card fraud is that the shipping and billing address usually vary. However, you can track down and reduce such cases by using AVS (Address Verification System).
1.2 SQL injection attack
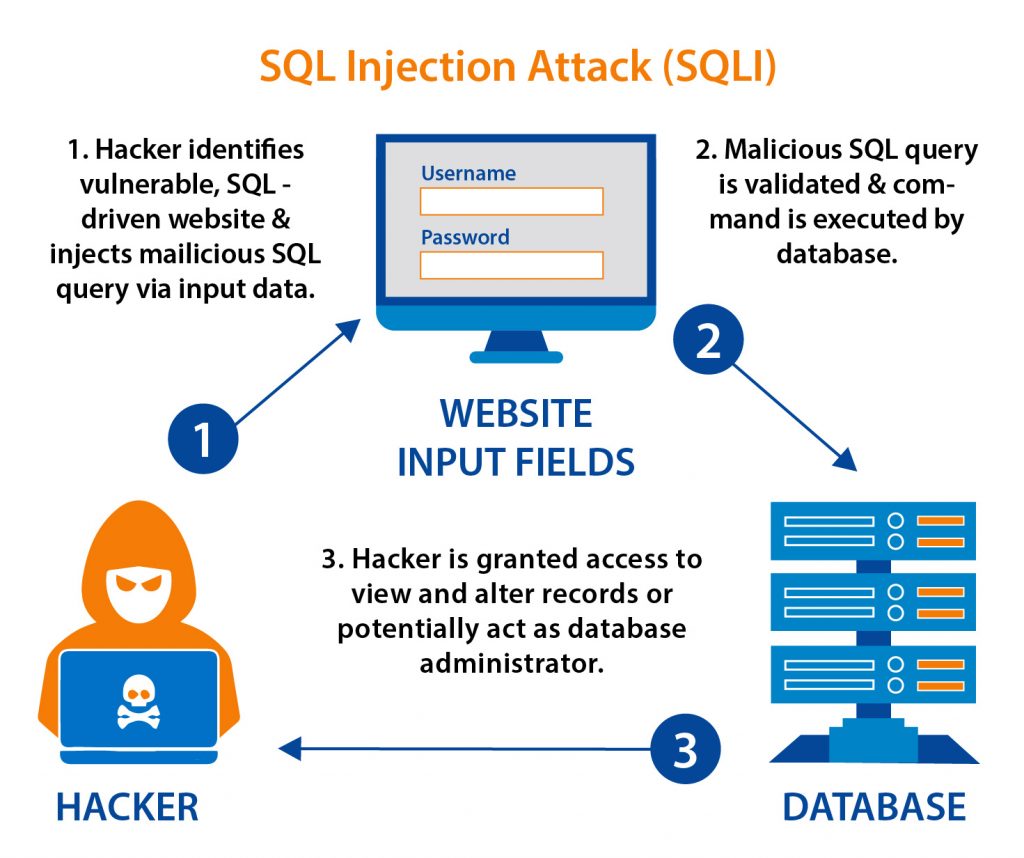
SQL injection attacks involve web security vulnerabilities that help attackers to interfere with the queries an application makes to its database. It generally allows them to approach confidential data that they are not normally able to access. Such data might include customers’ data or any other data that the application itself can access.
This type of ecommerce security threats should be detected soon because they can seriously harm your database, such as:
- Manipulate and modify the data
- Remove the entire database
- Steal credit card information
- Expose admin credentials, which may lead to further attacks
- Escalate the privileges
1.3 Malware injection
Hackers create 300,000 new pieces of malware daily.
This noticeable number was stated by McAfee. Malware is one of the most common and preventable cybersecurity threats. Malware might be unknowingly downloaded malware through harmful extensions, free software bundles, and even by simply using an open, unsecured Wi-Fi network.
A malware attack can cause a barrage of pop-ups, banner ads, competitor product recommendations, changes in your website’s appearance. Seriously, it can also flag your site with a warning and enter your site to the blacklist of search engines to protect users from visiting it. As a consequence, your website will be removed from search results.
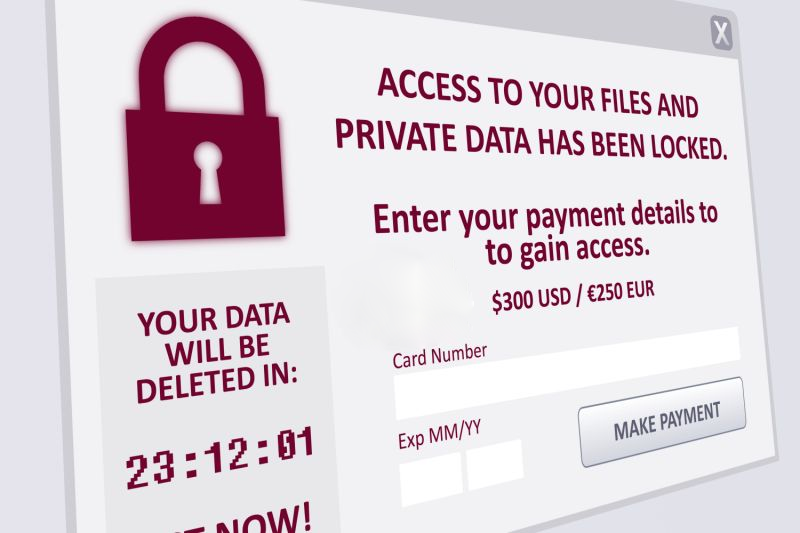
Ransomware is a typical form of malware that infects a computer and then demands a fee from the victim to recover access to the data. Users are shown instructions on how to do it to get the decryption key. Attackers execute this illegal money-making scheme by embedding malicious links in an email, instant message. Once the victim falls into the trap, they can lock the computer screen or encrypt important files with a password.
1.4 DDoS Attacks
If you are hosting your store on a server under your control, it’s important to defend it from (DDoS attacks) distributed denial of service attacks.
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt regular traffic of a targeted server or network by overwhelming the target or its surrounding infrastructure with a traffic strike.
Through this type of attack, hackers install malware, which affects your store’s functionality and hampers your server’s data. From time to time, malware will attack to steal confidential data of transactions. It has never been more crucial for merchants to follow security best practices.
1.5 Botnet attacks
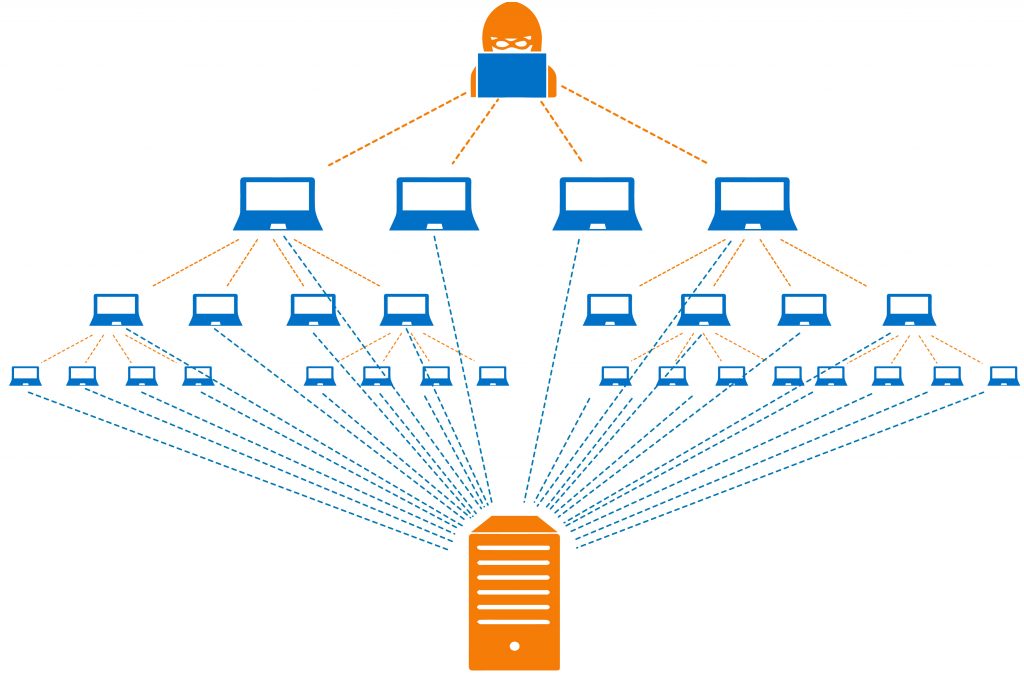
A botnet is a network including a lot of machines infected by malware that allows hackers to attack other machines (botnet attack). Botnet attacks involve malicious activities such as credentials leaks, unauthorized access, data theft, DDoS attacks, or sending spam emails from your address to many accounts.
Botnets are closely related to stealth oftentimes because the hacker’s interest is that the victim isn’t aware of the attack so that the botnet remains for the longest time possible. Once botnets compromise a machine on a network, there is a likelihood that all vulnerable computers on that network become infected.
1.6 Cross-site scripting (XSS attacks)
This ecommerce security threat is stated as one of the most rampant occurring yet easily fixable injection attacks faced by ecommerce websites. Through XSS attacks, attackers can run his/her scripts on a web page of your store.
In the typical example of a contact form, we usually see on any website, each of the entered inputs (name, email address, etc.) can be abused if the underlying code does not appropriately validate them. This is where attackers may insert a malicious piece of coding under Javascript code, HTML. The end-user has no reason to doubt the unreliable script and finally executes it. Then, the script can obtain access to any cookies, session tokens, or sensitive data.
The comment box is another approach for attackers to extract session cookies of those who open the comment box, where the malicious content is injected. So, validating inputs on arrival is the necessary process to prevent XSS attacks.
1.7 CSRF attacks
Unlike XSS attacks which exploit the trust a user has in a particular website, Cross-Site Request Forgery (CSRF) attacks hijack authenticated user’s sessions to submit a fake request they do not intend and exploit the trust that the site has in them. For example, users can be tricked to change their password into a password of the attacker’s choice, or edit the shipping address without the user’s knowledge or consent.
After a user clicks a URL that contains a malicious and unauthorized request, his/her browser will send this request to a targeted website with any related credentials like user session cookies. If this user is in an active session on that site, it understands this new request as an authorized request submitted by the user. That’s the way CSRF attacks work.
1.8 Website defacement
Website defacement is a type of ecommerce security threats that modifies the visual appearance of a web page. It is the consequence of defacers breaking into your web server and replacing the hosted website with one of their own.
Most times, the defacement is harmless. But it can sometimes be used as a distraction to conceal more dangerous behaviors such as uploading malware.
Website defacement affects content and causes lasting damage to the attacked site’s reputation by showing incorrect information or weird images. Vulnerabilities, poorly configured, or incorrectly maintained systems may be a reason that a site gets defaced.
1.9 Brute force attacks
Brute force is one of the least advanced but most successful techniques to break into a website. They perform attacks trying different username and password combinations with an automated tool or bot until they gain access, known as the trial-and-error method.
Once hackers get access, they can do anything with your website such as steal data, install malware, or even shut the system down. For this reason, it’s important to create a strong and complex password and change it regularly.
II – Common Magento Security Mistakes: The Way Hackers Approach Targets
Being one of the most popular ecommerce platforms worldwide, Magento provides global online merchants with a high usability and customization level. As of 2020, the platform serves more than 250.000 active online stores. Due to this popularity, Magento sites have become lucrative objectives of cybercriminals.
Magento sites are not exceptions to facing all the mentioned risks, which means that they’re also some of Magento security issues. Below, we’ve pointed out top critical mistakes or flaws that give hackers a chance to attack a Magento system.
2.1 Magento version
The Magento version that is being used on your website might be the first thing hackers pay attention to. Magento continuously launches new versions and updates to publicly disclosed security flaws of previous versions. Cybercriminals can research how to exploit those flaws. So if your Magento version hasn’t been updated, it could be at risk of being attacked.
Recently, Sanguine Security (specializing in preventing digital skimming attacks) stated that nearly 2000 websites using Magento 1 have been hacked during the weekend. The end of support for Magento 1 has left flaws for attackers who used malicious code to leak payment information from the targeted websites.
2.2 Third-party extensions/applications
Besides the Magento version, a third-party application is the second thing where hackers approach their targets. Even if it contains no public vulnerabilities, hackers are much more likely to identify a flaw if they investigate the code for an extension than in the Magento core.
Notably, it is not unusual for extensions to be tested carefully before installing it on your website. In contrast to self-coded solutions, the third-party extension’s code is public, making it easier for the attacker to figure out vulnerabilities.
Magento Website Maintenance can solve problems on websites that use an outdated Magento version or contain 3rd-party extensions’ vulnerabilities.
DISCUSS WITH EXPERTS for Magento Website Maintenance Service, which handles version & security updates, and further improvements!
2.3 Exposed admin login panel

Another cause of Magento security issues is that the administrative admin login panel is easily accessible. In our experience, we realize that many stores have their admin login panel located at “/admin.” Though this is not considered a vulnerability in itself, it makes it significantly easier for hackers to breach your website, especially if the access control requires username and password combinations only.
This situation creates the best condition for simple brute-forcing. Even when you create a complex and unguessable URL for the admin login panel, path disclosure vulnerabilities can be used to retrieve it. Therefore, keeping the admin login panel secure is one of the key pillars to avoid Magento security issues.
III – Top 3+ Websites for Magento Security Scan
For Magento users who haven’t known how to check website security yourself, these are 3 simple and easy-to-use tools that can be used for that. Just submit any website/webpage URL to those tools and wait for them to scan.
For in-depth troubleshooting, you’d better request the involvement of Magento Maintenance Experts.
3.1 MageReport

MageReport checks is a free Magento security scan tool that reports to you all known vulnerabilities of your website and even commonly used 3rd party extensions, including:
- Admin disclosure
- RCE/webforms vulnerability
- Cacheleak vulnerability
- API exposed
- Credit card hijack
- Ransomware
- Gurulnc Javascript hack
- And much more…
3.2 Sucuri
Not specific for Magento security scan, Sucuri is a helpful tool to test various components of a website. With a free scan, the tool does not detect malware on your site. If you still suspect being hacked, you can consider using a paid plan for a complete scan, manual audit, and guaranteed malware removal.
For security check, after scanning your website, Sucuri returns the information about:
- Malware
- Blacklisting
- Injected SPAM
- Defacement
- Outdated version
3.3 Foregenix
In addition to MageReport and Sucuri, Foregenix also allows users to monitor Magento websites’ security status and finally turns out a high-level report of the following aspects:
- Magcart and derivatives
- Outdated software or security patches
- Ransomware
- Magento Backdoor Trojan Module
- Magmi vulnerability
- Unprotected version control
Wrap Up
Ecommerce security threats do not exclude any website of any platform. However, we can prevent significantly the possibility of risks by following the best practices to secure ecommerce websites. For this reason, we’ll back soon with a noticeable topic on Magento security best practices.
If you are facing problems with Magento, why don’t you look through our best Magento 2 Services? It’s always a great honor for us to actualize your needs with your highest satisfaction.
