Recognizing the constant risk to the integrity of your online store is crucial, as it is often susceptible to breaches through third-party applications, plugins, API integrations, and patches. Magento 2 security best practices are not just a recommendation but necessary for every online store owner. These practices protect your store from threats, safeguard sensitive customer data, and ensure smooth business operations. Therefore, understanding how to secure Magento 2 is crucial to proactively address potential vulnerabilities and safeguard your online store.
Now, scroll down to get details about these tips:
Magento Security Issues
Table of Contents
CVE-2024-34102 is a critical vulnerability for Adobe Commerce and Magento as it is a pre-authentication XML External Entity (XXE) injection. Malicious actors can exploit this without authentication which can lead to data exfiltration, unauthorized access, and even remote code execution. Given the severity and impact, you need to act now to protect yourself from exploitation.

Reasons Why You Need to Check Security in Magento 2
Almost all Magento online stores handle sensitive data – customer information, financial details, and more – security. A breach can lead to financial losses, reputation damage, and customer trust erosion. This section will go through the reasons why security is a priority in your Magento 2 store:
1. Protection of Sensitive Data. Magento 2 has a lot of sensitive data, customer info, payment details, and personal credentials. Having security in place helps to prevent unauthorized access and breaches. Magento 2 has data encryption, secure payment gateways, and custom access controls to protect sensitive data.
2. Maintaining Customer Trust. Customers trust eCommerce platforms with their personal and financial info. Any breach or security incident can break that trust and harm your brand. Having security best practices in place, like using HTTPS/SSL for data transfer, keeping Magento and its extensions up to date, and having strong password policies helps to maintain customer trust and loyalty.
3. Preventing Financial Loss. Fraud and cyber-attacks can cost your eCommerce business a lot of money. Magento 2 has various tools and extensions to prevent fraud like automated risk assessment, order screening, and integration with leading fraud detection tools. These help reduce chargebacks, avoid spam and fraud, and comply with PCI standards.
4. Mitigation of Cyber Threats. Cyber threats are always evolving and eCommerce platforms like Magento 2 are the target. Regular security audits, software updates, and implementing best practices like Two-Factor Authentication (2FA), CSP and IP restrictions can help to mitigate these threats.
10+ Magento 2 Security Best Practices You Should Leverage
Ensuring the security of your Magento 2 store against cyber threats is crucial for the prosperity of your online enterprise. Given the growing complexity of cyberattacks, adopting strong security protocols has become imperative rather than optional.
The following section showcases key Magento 2 security best practices aimed at protecting your store, customer information, and overall reputation:
#1. Update to the Newest Version
Whenever a new version of Magento is released, it has security fixes for known issues from previous versions. By keeping your site up to date with the latest version you are protecting it from known security risks. Magento also improves its security features to defend against new threats. New versions have better encryption, stronger authentication, and more security settings. Following industry standards like PCI DSS is important for sites that handle sensitive payment information.
In addition, bug fixes and performance improvements in new versions will make your site more stable and secure. Being on the latest Magento version gives you access to community support and best practices for securing your site.
>>> Checkout the comprehensive guide on How to Upgrade Magento to 2.4.7 Version [2024 Update]
#2. Implement Two-factor Authentication (2FA) for Admin and SSH Connections
Two-factor authentication (2FA) is like adding a second lock to your front door. Instead of just using a key (your password), you also need something else, like your phone, to get in. This makes it much harder for bad guys to get in, even if they know your password.

Passwords can be stolen or guessed, but with Two-Factor Authentication (2FA), even if someone gets your password, they still need your phone to get into your account. This stops hackers from getting into your stuff, especially if they tricked you into giving them your password. Using Two-Factor Authentication (2FA) is like following the rules to protect your info. Many places require it to keep your data safe.
All in all, Two-Factor Authentication (2FA) is a simple way to make your online accounts much safer by requiring two different ways to prove who you are.
#3. More controlled administration with module
Go to Amin Panel ⇒ Admin Action Log ⇒ Admin Logs Grid to keep track of admin actions, control roles & undo risky actions.
Why Should Use Magento 2 Admin Action Log Module?
The Magento 2 Admin Action Log is an extension designed to assist merchants in overseeing the actions of admin users within the backend, thereby mitigating vulnerabilities and minimizing the consequences of configuration errors. It provides thorough oversight of the admin panel by controlling access to the log report and recording critical details regarding backend modifications, including the initiator, the type of the alteration, location, and timestamp.
Here’s its key functionalities:
- Identify the categories of administrative actions that are automatically documented and reported
- Restore modifications with a single click
- Review all administrative working sessions from initiation to completion, with real-time activity monitoring
- Manage the navigation history of administrators
- Arrange logs in a grid format for straightforward tracking and sorting
- Set a time frame for log clearance
- Observe changes in quantity within the log
- Automatic email notifications are dispatched upon any changes in quantity
#4. Secure the Admin Account & Admin Panel URL
The Magento admin panel is typically accessible via a standard URL structure, such as “/admin” or “/backend”. This predictability renders it vulnerable to malicious individuals who may seek to exploit weaknesses or initiate brute-force attacks.
A custom admin path restricts direct access to the admin panel unless the specific URL is known. This measure serves to discourage unauthorized users from attempting to access critical administrative functions, including order management, customer information, or website configurations.
Therefore, store owners can create additional challenges for attackers seeking to exploit known vulnerabilities or gain unauthorized access.

To secure admin:
- Add a secret key to URLs
- Make passwords case-sensitive.
- Limit admin sessions, password lifespan, and number of login attempts.
- Timeout keyboard inactivity before the session ends.
- Make usernames and passwords case-sensitive.
- To protect Admin from automated brute force attacks, enable reCAPTCHA.
- Use strong passwords and share account login information through a secure platform
When granting Admin permissions to roles and assigning roles to Admin user accounts, it is prudent to adhere to the principle of least privilege.
#5. Limit access by IP Address

To improve the security of your administrative panel, consider restricting access according to IP addresses. This measure ensures that only users from designated IPs are permitted entry, thereby minimizing the risk of unauthorized access. However, it can be inconvenient as you’ll have to constantly update members’ IPs in case of working remotely or outside the office.
To implement IP address restrictions, modify the .htaccess file found in the pub/ directory of your Magento installation. You will need to insert the following lines, substituting ALLOWED_IP_ADDRESS with the specific IP addresses you intend to authorize:
<FilesMatch "index.php"> Order deny,allow Deny from all Allow from ALLOWED_IP_ADDRESS </FilesMatch>
It is advisable to routinely update this list of IP addresses, as the IPs of your team members may vary over time or when they are working remotely.
#6. Safeguard Your Website and Infrastructure
Block unauthorized access
Work with your Magento hosting provider to create a VPN tunnel to protect the site and customer data from unauthorized breaches. Use an SSH tunnel to access the Commerce app.
Use a Web Application Firewall (WAF)
Use a Web Application Firewall to detect unusual traffic patterns, like credit card info being sent to unknown IP addresses. Adobe Commerce on cloud services has built-in WAF with Fastly services. It defends against web-based attacks like SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks. With WAF, you can secure your Magento store, control incoming traffic, block malicious requests, and keep your store performing well even during high traffic or DDoS attacks.
Set up strong password policies
Make sure your passwords are strong and change them every 90 days as per PCI Data Security Standard recommendations.
Use HTTPS
Launch the whole site in HTTPS for new Commerce sites. This is a ranking factor for Google and users trust sites that are secure for online transactions.
Run security scans
Run your Adobe Commerce and Magento Open Source sites through the Commerce Security Scan tool. This free tool allows you to scan for potential security threats, malware, and unauthorized access attempts. It also gives you alerts for emerging vulnerabilities. Detailed reports to help you fix website security issues. Stay up to date with patch releases and security alerts by subscribing to notifications.

#7. Privacy Policy
Remember to update the Privacy Policy page on your Magento 2 store to well inform online users about what type of data your business will collect and how such information is processed. Also, as cookies are tightly under GDPR law, you must include a brief overview of how cookies are handled to be linked to that Privacy page.
In Magento Admin, to edit the Privacy Policy page, please follow the Content ⇒ Elements ⇒ Page ⇒ Privacy Policy ⇒ Action ⇒ Edit.
#8. Protect Extensions and Custom Code
1. Choose a partner or solution integrator (SI) with a security focus: Select companies that have a secure development methodology to ensure safe integrations and custom code delivery.
2. Use secure extensions: To ensure extensions for Commerce deployments are secure and suitable, talk to your solution integrator or developer. Only use extensions from the Adobe Commerce Marketplace or through your solution integrator and make sure the extension license is transferable. Minimize risk by minimizing the number of extensions and vendors involved, before integrating a review of the extension code for security vulnerabilities. PHP extension developers should follow Adobe Commerce guidelines, processes, and security best practices and avoid PHP functionality that can lead to remote code execution or bad cryptography.
3. Code audit: Check your server and source code repository for any leftover development artifacts. Make sure log files, .git directories, SQL tunnels, database dumps, php info files or any other unnecessary files not protected are not public facing. These files can be exploited during an attack.
#9. Stay Compliant with PCI Standards
The Payment Card Industry Requirements (PCI) refers to businesses accepting online payment via credit card to protect card brands, merchants, as well as customers.
Since payment is indispensable to eCommerce procedure, Magento 2 store owners must process sensitive data, including customers’ personal information and credit card numbers, which are attractive targets of cybercrime to track and make unauthorized transactions.
It is also essential for store owners to be vigilant about security practices, as poor security can lead to situations where not only financial information but also mobile devices are at risk if your phone is tracked by malicious entities. Failing PCI compliance means not just the monetary penalty imposed by card issuers you have to pay but also customer dissatisfaction and your brand reputation.
Trust takes years to build, seconds to break, and forever to repair!
Much as PCI Compliance is essential, don’t worry too much as we provide you with a checklist to make your Magento security fit well with the requirements:
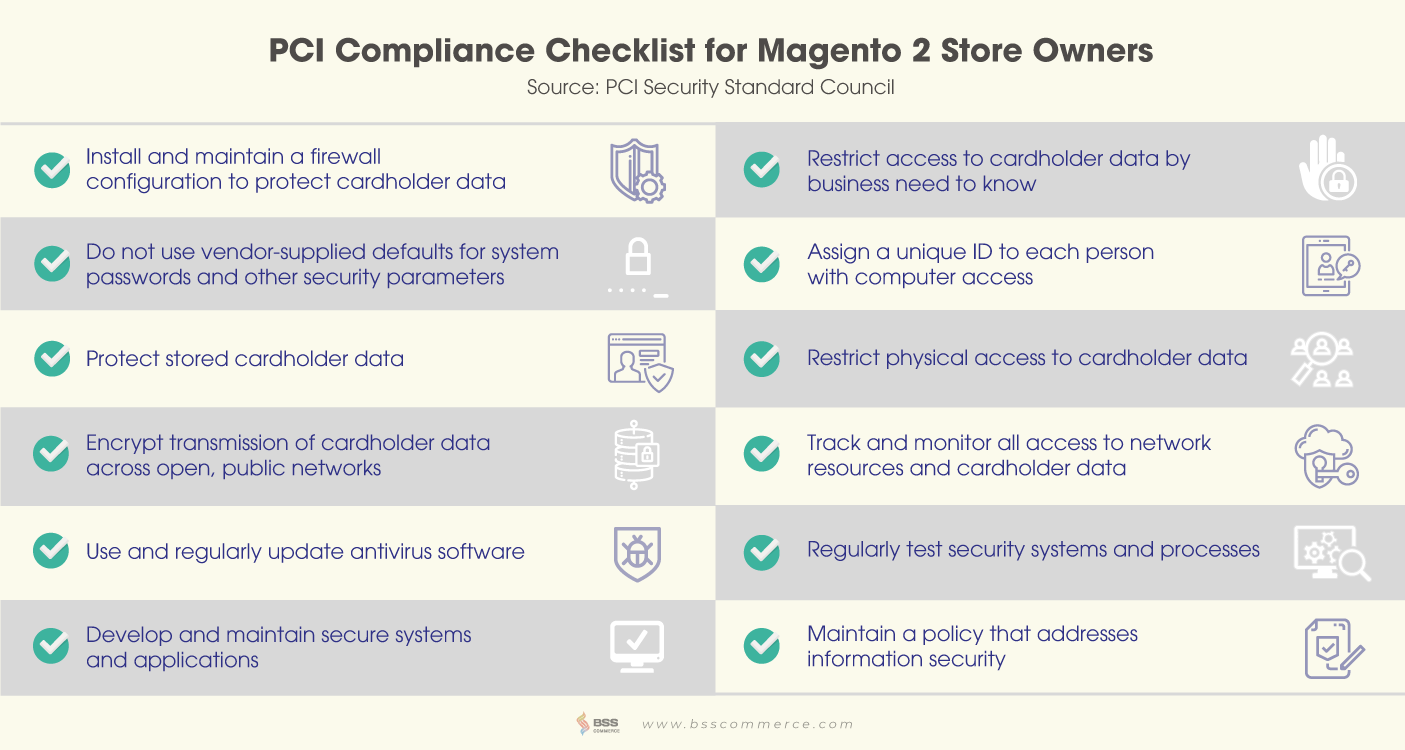
In brief, there are six steps you need to follow:
- Build and Maintain a Secure Network
- Protect Cardholder Data
- Maintain a Vulnerability Management Program
- Implement Strong Access Control Measures
- Regularly Monitor and Test Networks
- Maintain an Information Security Policy
#10. Defend Against Malicious Software
Hackers are always coming up with new ways to get credit card info and personal data from transactions. Here are a few common types of attacks Adobe Commerce recommends customers watch out for:
- Website defacement: Cybercriminals change the visual parts of a site, which blocks access but keeps payment info safe.
- Botnet: Customers’ servers get added to a botnet and you might get spammed or participate in a Distributed Denial of Service (DDoS) attack.
- Server intrusions: Data breaches, malware installation, and website downtime.
- Silent card capture: Attackers deploy hidden malware or modify the checkout process to capture credit card info for sale on the dark web.
- Stealthy keylogging: Malicious actors keylog to capture admin user credentials to go undetected.
In the event of a security incident on your Adobe Commerce site hosted on a cloud infrastructure, do:
- Audit all admin user accounts.
- Enable advanced multi-factor authentication (MFA).
- Save logs.
- Check for security patches for your Adobe Commerce version.
Work with system integrators and security experts to investigate and remediate the situation. Determine the scope of the breach, and the attack vector and take necessary actions including data wiping and reinstalling, removing unnecessary files, and resetting all credentials and keys.
The next step in incident analysis is to gather facts quickly. Adobe Commerce has tools for this, such as Magento 2 Admin Action Log Module, Adobe Commerce Observer, and New Relic Logs. These tools provide information and analytics to help you identify the root cause of incidents and optimize performance.
Some best practices should be implemented:
1. Audit Accounts, Code, Database. This checklist outlines what to audit for administrative user accounts, code, database configurations, and logs. Must-dos include checking and removing old or suspicious accounts, updating passwords, checking security settings, and checking code integrity and database security.
2. Remove Google Warnings. If Google flags a site for malicious code, you need to request a review after the site is cleaned up. The review process for a site with malware can take several days. Once Google verifies the site is clean, any search result issues and browser warnings should be resolved within 72 hours.
3. Malware Results Checklist. If publicly available malware scanners confirm malware, investigate thoroughly. Work with the solution integrator to remove the malware from the site and follow the recommended remediation steps.
4. Perform Additional Reviews. Work with experienced developers, external experts, or solution integrators for complex attacks to get the site back up and do a full security review.
#11. Close Email Vulnerabilities
Email security is crucial for Magento stores. Hackers often use email to trick customers into giving up personal information, like passwords or credit card details, through phishing scams. These attacks can steal customer data and damage a store’s reputation.
Email is also used for important things like resetting passwords and confirming orders. If hackers can mess with these emails, they can take over customer accounts or steal money. Protecting your store’s email system is essential to keeping customers and their information safe. It also helps you follow important rules about data privacy and security.
#12. Choose a Reliable Hosting Provider
A reliable hosting provider is like a bodyguard for your online store. They have special tools to keep the bad guys out, like strong doors (firewalls) and alarm systems (intrusion detection). They check for problems often to make sure your store is safe.

The bad guys can try to crash your store with a lot of traffic at once (DDoS attack). A good hosting company can stop these attacks so your store keeps working. Your hosting company keeps your store in a safe place with lots of locks and cameras. They also make copies of your store’s information in case something bad happens.
They also use special codes to keep your customer’s information safe when they visit your store. This is like sending a secret message that only you and your customer can understand. So choosing a good hosting company is like hiring a bodyguard for your business. You’ll sleep better knowing your store is safe.
#13. Guard Against SQL Injection
MySQL injection is a big threat to Magento stores. Hackers can exploit the website to steal customer info like addresses, payment details, and order history. This can lead to massive data breaches, damage to business reputation, and huge financial losses.

MySQL injection attacks are a threat not only to data integrity but also to the operational stability of Magento websites. Malicious actors can execute harmful SQL commands that can delete or alter critical data and cause website downtime, revenue loss, and bad user experience. Preventing MySQL injection is key to securing the integrity and availability of the Magento platform.
So, preventing MySQL injection in Magento is key to data security, data breaches, financial loss, website integrity, and compliance. It’s part of the overall security for an eCommerce website built on Magento.
#14. GDPR Compliance
It has been nearly three months since the General Data Protection Regulation (GDPR) officially went into force in May 2018. Though you might be aware of this personal data protection law, let us remind you of several vital components.
- GDPR covers various fields of personal data protection. Hence, its regulations are extensive
- Monetary fines might be up to €20 million or 4% of your annual global sales you might get affected even if your business is not in Europe Magento service as Magento is always backup GDPR Compliance Efforts
Complete Get Cookies Compliance under EU GDPR
>>> KEEP READING: All Magento 2 Users Need to Know about GDPR Compliance
The Bottom Line – Magento Security Best Practices
In short, the above Magento 2 security best practices checklist is the must-read to keep online merchants from operation error, loss of merchandise, financial and reputation damage, or even lawsuit threats. Further is to protect customers against identity theft and data exploitation.
The keys of how to secure Magento website you must take home:
- Hire professionals: hosting service, web developments, extensions, themes, etc.
- Secure system requirement and Magento 2
- Use the most recent updates: software, version, security patches
- Be not taken for a ride with suspicious things
- Monitor Magento 2 security frequently
- Stay calm and well-prepared.
We are willing to give you a helping hand to Magento 2 security problems at all times, so feel free to take a tour around and contact us. We are BSS Commerce.
FAQs – Magento 2 Security Best Practices
1. What happens if a security breach on an eCommerce site?
A security breach on an eCommerce site can result in big fines and penalties. This can be from not following data protection regulations and damage to the company’s reputation which can scare off potential customers. Also, it can disrupt business operations, inventory management, sales activities, and shipping procedures.
2. How can merchants secure Magento?
Magento store owners can secure their sites by choosing a reliable hosting provider, installing a security plugin, and performing regular penetration testing and regular data backups. Plus, using Captcha for administrative logins and subscribing to Magento’s security alerts can really help protect the site from hacking attempts.
3. How can access control help my Magento store?
Access to sensitive parts of your site is restricted to trusted administrative users through an access control feature. This reduces the attack surface. Use strong passwords which should have a mix of uppercase and lowercase letters, numbers, and symbols, and limit the number of admin accounts.
4. Which security plugins are available for Magento ecommerce and how do they stop hackers?
Magento security plugins are specialized software that helps to secure eCommerce platforms. These extensions add an extra layer of protection against hackers by strengthening login security, identifying potential vulnerabilities, and running security checks.
Here are some extensions and tools you need to know:
- Magento Security Scan Tool
- Web Application Firewall (WAF)
- Magento reCAPTCHA
5. What are best practices for backup and why is it important for Magento stores?
Backups are crucial for security, to protect your data from incidents or cyber attacks. Best practices are to back up regularly, use multiple media store them in a secure location, and verify the data after restoration. A consistent backup process ensures that in case of a breach your ecommerce platform can recover quickly with minimal data loss.
6. How does a security policy influence the safety of a Magento website, taking into account security plugins and web browsers?
A well-structured security policy is essential for safeguarding a Magento domain in various significant ways.
- First, it covers user credentials management and requires strong passwords and access controls so less chance of unauthorized access.
- Second, it outlines security extension implementation so Magento platform security is enhanced and vulnerabilities are fixed.
- Third, it sets the rules for how browsers interact with the store, including secure (HTTPS) connections and Content Security Policies to prevent cross-site scripting (XSS) attacks.
- Fourth, it has a process for security audits, penetration testing, and patching of vulnerabilities. So a well-thought-out security policy is a complete defense in depth.



