Recently, on Jan 13th, Magento just released an urgent update regarding the newly found vulnerability in any Magento 1 and Magento 2 stores using Sendmail. You can easily see a popup marked as critical notifying about this update when logging in the backend.
This comes from a vulnerability in a Zend Framework 1 and 2 email component. Since both version of Magento now is using this two framework, hence they will be affected by it. In the announcement, Magento stated that the vulnerability is serious and also warn a high risk of a remote code execution attack if your stores are choosing Sendmail as a mail transport agent.
About the exceptions, business owners choosing a third-party mail provider like MailChimp, Sendy, Mailgun… , you do not need to worry about the exploit. And Enterprise Cloud Edition users are also safe from the issue since no risk was detected while checking the configuration.
For Sendmail users, don’t be worried too much, a temporary solution was updated by changing the mail sending settings. The settings are originally used to control the “Reply to” address for emails sent from your Magento store. Please access the back end by the following path:
+ Magento 1: System-> Configuration-> Advanced-> System-> Mail Sending Settings-> Set Return-Path
+ Magento 2: Stores-> Configuration-> Advanced-> System-> Mail Sending Settings-> Set Return-Path
In Set Return Path, choose No to protect your site from high attack risk.
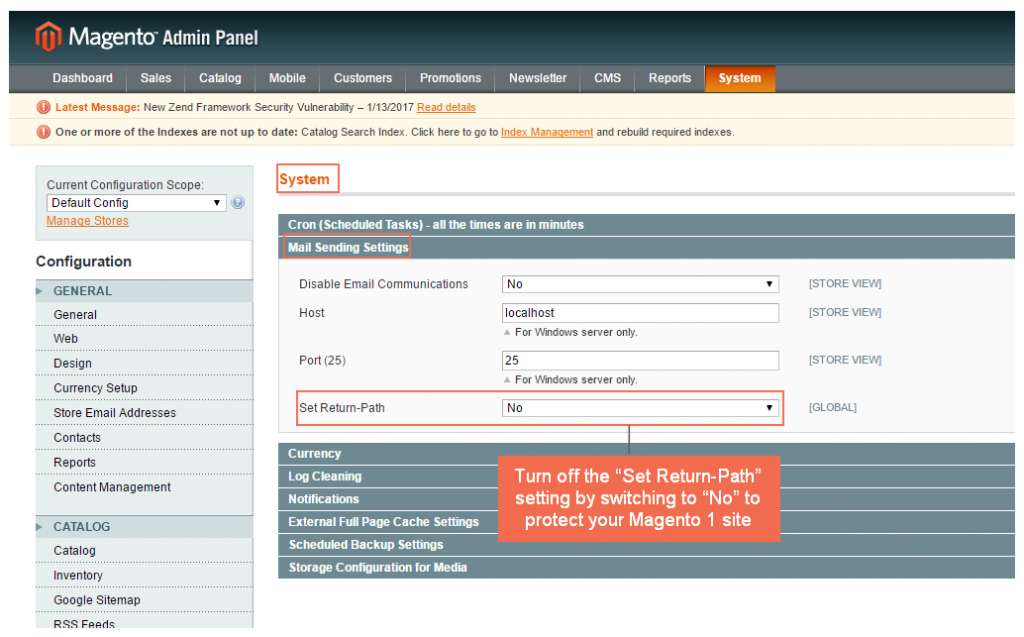
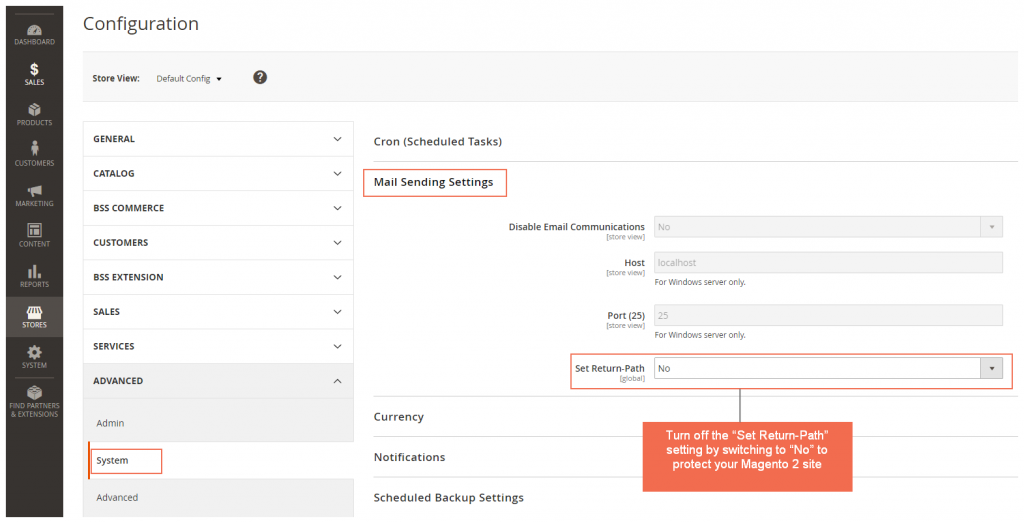
Even no attacks based on this vulnerability is recorded until now, Magento still gives a high warning for this. Thus, it is essential that if you are using Sendmail and configuring “Set Return-Path” to “Yes,” please immediately switch off by choosing “No” to prevent your site from the exploit.
Security patches are in the fast progress of developing, and Magento hopes that they can release it within the next few weeks. We will update instantly once there is more news regarding the case so please regularly visit our blog.
You can read the full announcement from Magento here.
